 Convenient User Interface Convenient User Interface |
|
| - Easily perform scanning, check scan results and history, and generate reports. |
|
 Comprehensive Reporting and Analysis Comprehensive Reporting and Analysis |
|
| - Provides detailed reports and analysis to help understand vulnerabilities and take corrective actions to enhance security levels. |
|
 Fast and Various Scanning Fast and Various Scanning |
|
| - Various effective scan methods such as General Scan, Manual Scan, Scheduled Scan and Group Scan. |
|
 Highly Security-Safe Methods Highly Security-Safe Methods |
|
| - Provide Encryption of Collected Data From Target Assets and Their Scan Results. |
|
|
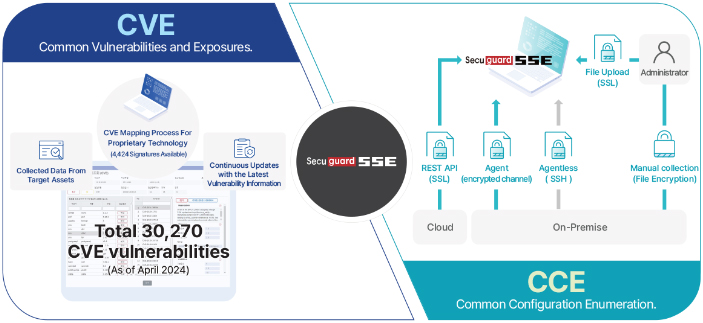
Our solution offers integrated vulnerability assessment,
addressing both system configuration weaknesses (CCE) and software vulnerabilities (CVE). |
 |
|
